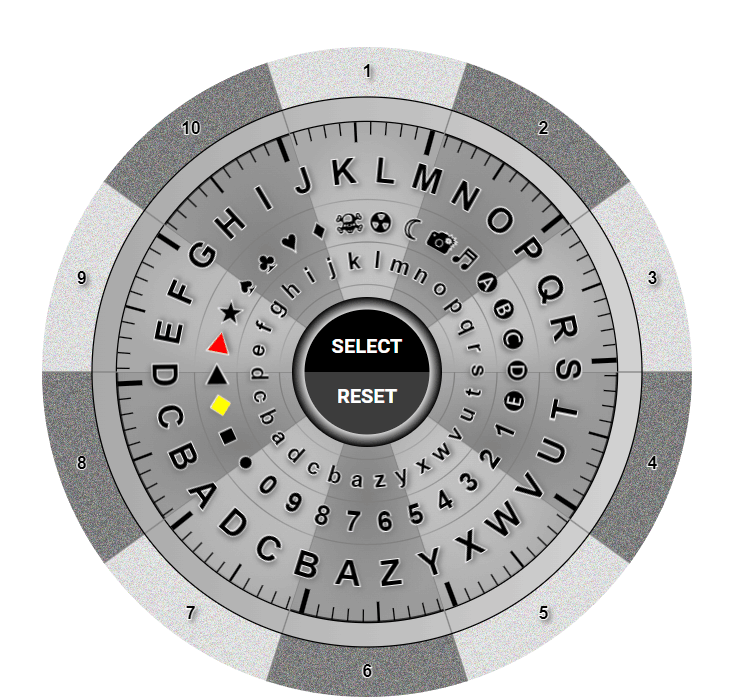
Easy to use
You simply in your mind pick a section (1-10) as shown above, and like a safe dial turn it so the letters in your password rest in the section you are thinking of.
Only you know what you are thinking of, that information is never entered which is key in proving your authentication.
Enhanced Security:
Access Defender significantly mitigates the risk of credential theft by eliminating password transmission, thereby protecting against interception, hacking, and recording. This enhancement bolsters the overall security posture for both individuals and organizations.